One of the most useful services to any home labber is a VPN, so that you can access your home network from anywhere and browse as if you’re at home. That not only lets you use any self-hosted services you have on your NAS without having to open ports to the wider internet, but it also circumvents any geo-blocked services and nicely encrypts your data, so nobody can snoop in.
This works well, but there’s another issue that crops up when you have a mix of servers, containerized services, and other things in your home lab. It gets downright annoying to connect to them by IP address and port, and it’s much simpler to set up a reverse proxy to simplify access and management from a single IP. Inside, you translate incoming requests to the domain name of the self-hosted apps, and you can even set up nice dashboards to make things even easier.
I’ve used various VPNs, from self-hosted WireGuard to ZeroTier and Tailscale, alongside various combinations of reverse proxies, which work well but have the annoyance that you’re managing two services at all times, and they’re not all managed with easy-to-read web interfaces.
But then I found Pangolin, and everything clicked. Here was a self-hosted reverse proxy management server that deploys easily, has Traefik and WireGuard tunnel clients, and also has access control. It’s essentially a Cloudflare Tunnel, but you’re self-hosting it, so everything is under your control, and it’s rapidly becoming my favorite reverse proxy and VPN solution.

Related
9 reverse proxies you should check out for your home network
If you’re self-hosting any services, you’ll want a reverse proxy as another layer of defense.
What is Pangolin? Why would you use it?
Manage your reverse proxy with this self-hosted management server with authentication and more
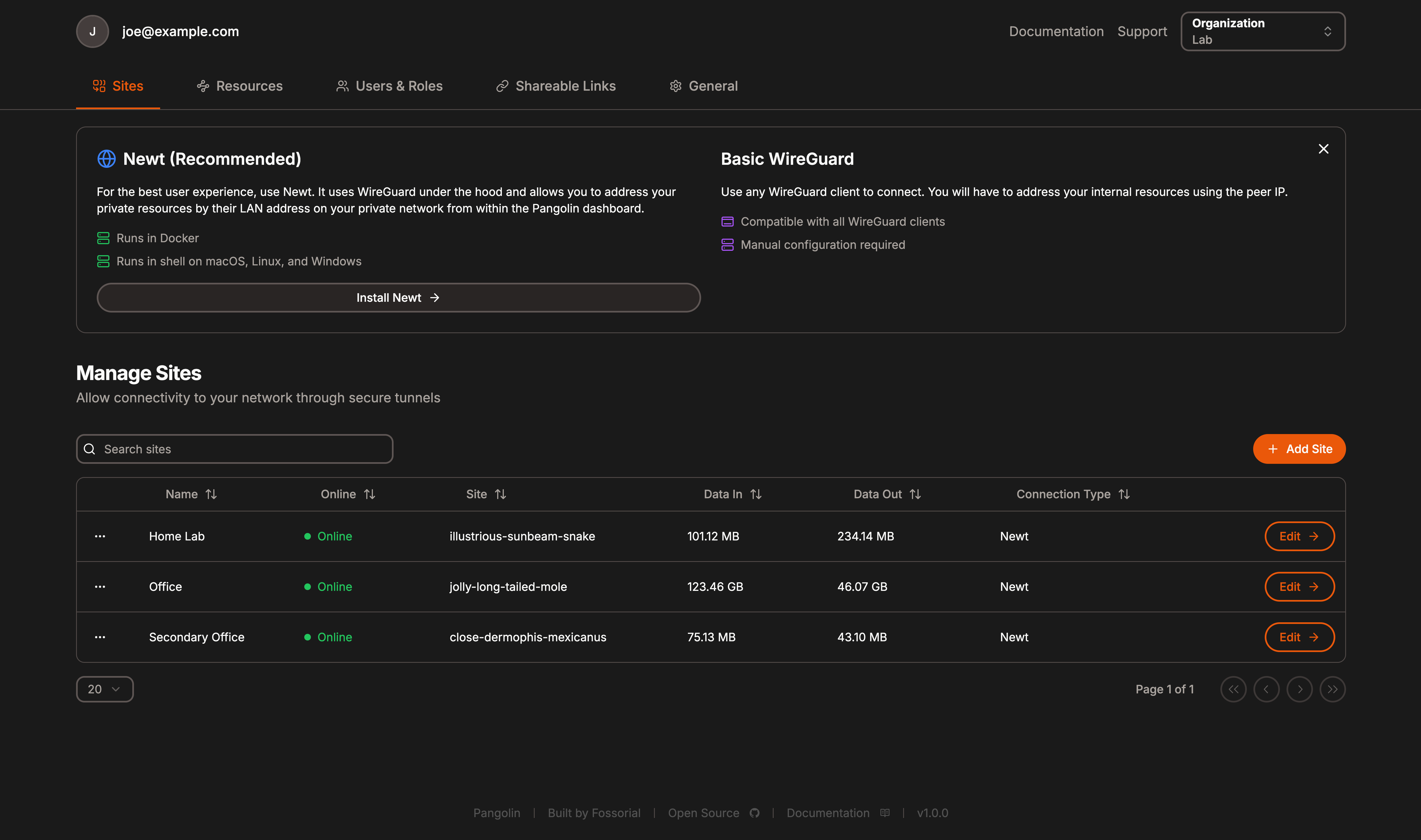
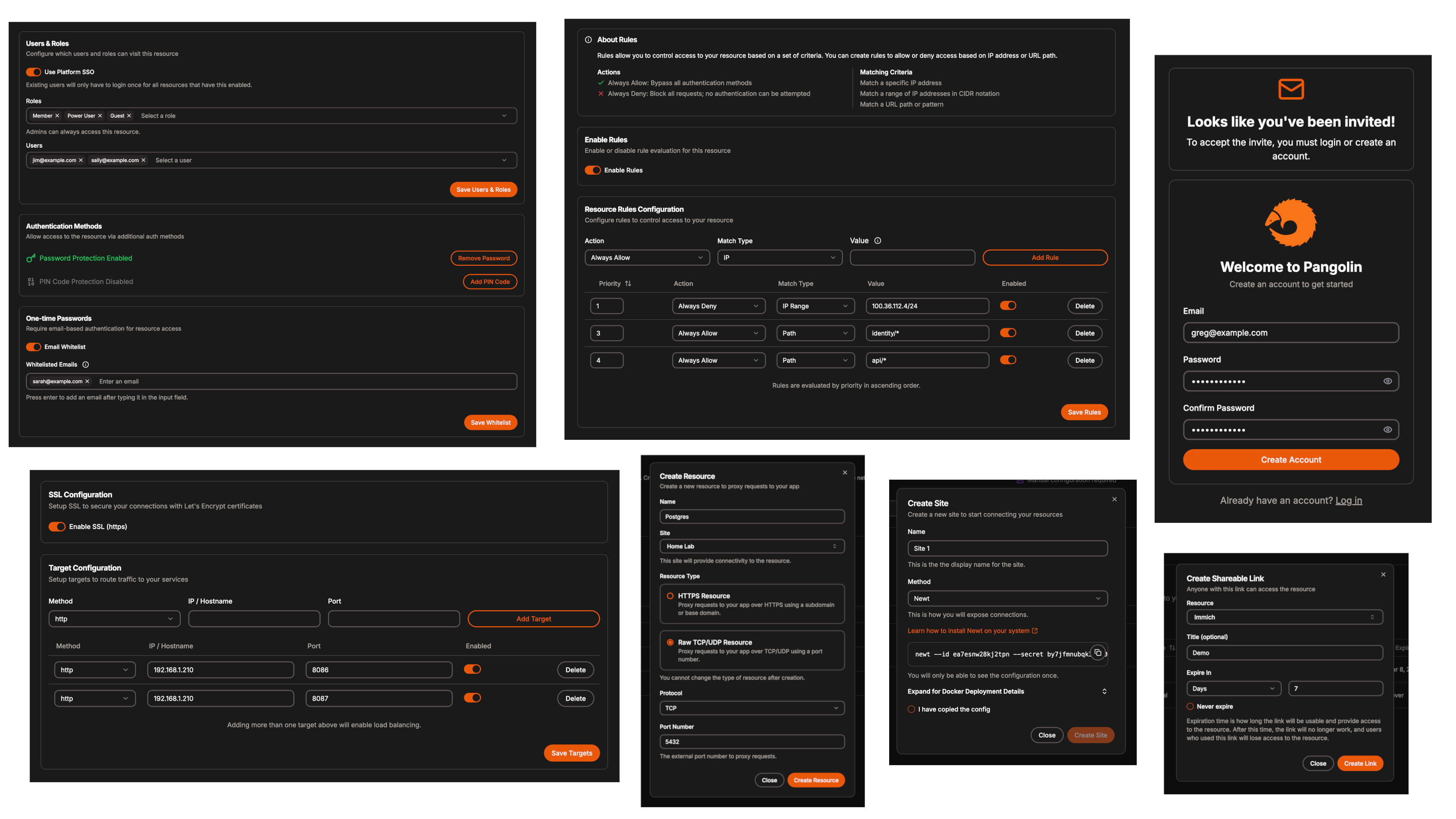
Pangolin made me very excited when I started reading the documentation, because it does so many things that you’ll want as a home labber, and it does them in an effortless, stylish way. Imagine Nginx, Authelia, and Cloudflare Tunnel in one package, but able to be self-hosted on your own VPS or server, so you’re always in control. It builds on WireGuard and Traefik to do so, with a custom management application and central server, several custom plugins, and a custom WireGuard client. Those components include:
- Pangolin: Management server
- Gerbil: WireGuard interface management
- Traefik: Modular reverse proxy with extensibility
- Badger: Traefik plugin for authentication
- Newt: Minimal user space WireGuard client
Because it uses WireGuard tunnels, you don’t need to open any ports on your firewall or router. This makes it perfect for users behind restrictive CGNAT, DS-Lite, or strict ISP firewalls, as it can punch straight through the NAT and connect to your self-hosted apps without exposing them. It’s deployed in minutes thanks to Docker, and once the web-based interface is up, it walks you through getting the rest of the connections set up. It’s all incredibly simple, and now I don’t need to worry about CLI commands or SSH’ing into my reverse proxy to get things connected.

Why is Pangolin better than the alternatives?
Simplicity and security, but that’s not all
Using Pangolin has a few big benefits over traditional reverse proxies, but the biggest for me is that it doesn’t need any ports opened to work. Plus, it’s got centralized SSO with role-based access control and support for 2FA to make things even more secure. It automates SSL management with Let’s Encrypt, is built with Zero Trust, and is self-hosted, which is a massive plus over many of the other comparable services.
It’s modern, has modular plugin support for anything Traefik can use, is easy to deploy with Docker Compose, and has load balancing built in. It’s security-focused, has built-in tunneling, and makes your home lab much easier to manage.

Related
Is Tailscale the safest way to access your home network remotely?
Tailscale is easy to set up, but is that trading off your security?
Why I stopped using Nginx and WireGuard
Or more precisely, why I don’t want to manage it myself anymore
Nginx might have been around for a long time, but it’s not the easiest to use or most stable reverse proxy. It’s also missing extensibility, which the Traefik-based reverse proxy in Pangolin enables, among other things, so you can add cybersec modules like CrowdSec, Fail2Ban, and Geoblock. Even using Nginx Proxy Manager isn’t the easiest thing to use, and while it has Let’s Encrypt baked in, it doesn’t have the VPN power of Pangolin either.
WireGuard is easier to use, for sure, but it needs your firewall and router at home to open some ports to the outside to work. Pangolin and the Newt client sidestep that, creating encrypted tunnels without needing any port forwarding setup. All you need is the Newt client running on your NAS or server that has self-hosted applications, and the central Pangolin server does the hard work for you. Going to your own domain name and logging in with your Pangolin creds gives you access to all your self-hosted applications, and it’s awesome.

Related
4 reasons you need to use WireGuard instead of OpenVPN for connecting to your home lab remotely
If you have a home lab and want to connect to it remotely, WireGuard is much better than OpenVPN.
Being able to self-host a management server for my VPN and reverse proxy needs is a game-changer
Pangolin isn’t just a fantastically easy-to-configure VPN and reverse proxy; it’s a revelation in self-hosting simplicity. It gives you an authenticated dashboard on a domain you control to access all your self-hosted apps securely via encrypted tunnels. It even supports 2FA, making it about as secure as any other services you use, but it’s all owned and controlled by you, so your data isn’t being used elsewhere.
There are even tons of things on the roadmap for future inclusion, like automated Crowdsec installation for deeper protection, IP and path-based rules for bypassing auth when needed, and full multi-domain support with SSO. I can’t see myself using anything else for accessing my self-hosted apps, because it takes all the drudgery out of the setup.

Related
5 reasons ZeroTier is the best Tailscale alternative for your home lab
There’s a million ways to connect to your home lab, but some options are better for your needs.